Download Project Document/Synopsis
A security breach can be a threat to national confidential data or the private data of an organization or a person. The most popular kind of password used for security purposes is text-based. However, these passwords can be easily breached and one may lose his/her private data to the wrong hands. With the rise in cyber-crime, security threats related to logins & accesses have become a major concern. Also, the use of single security authentication is not sufficient enough to keep you protected from cyber threats.
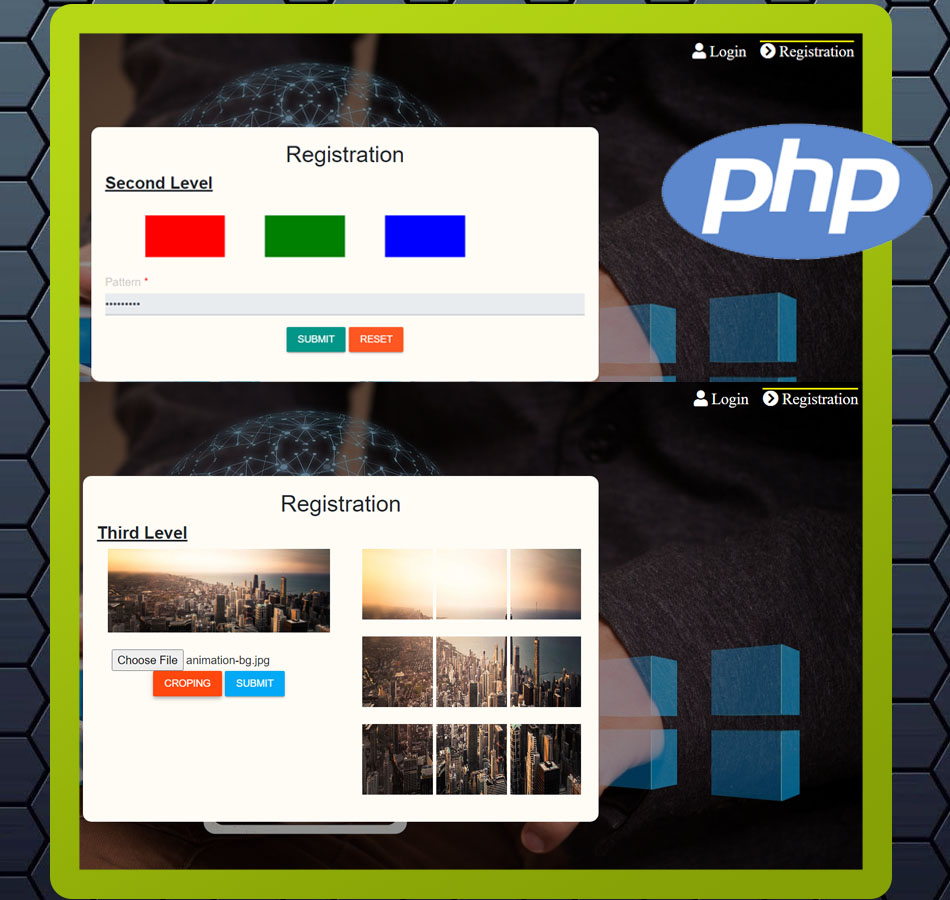
Hence to increase the security level we have developed a Three-Level Password Authentication system that will make sure that only the authorized person will have access to the system or data. This system contains three-level logins having three different kinds of password systems. The project comprises a passphrase, image-based segmentation password, and graphical password. The password difficulty increases with each level making the access more secured. In this way, this PHP-based Three Level Authentication System will help the users to keep their data safe from any hackers & cyber threats.
In this System, while user registration, user will be asked to setup three level password for security purpose first level is the conventional password system i.e. texted password, second level is image-based password and third level is graphical password method. For Login User need to Login to check the security by entering three level password-authentication. As user start entering password, the first level will authenticate the user by matching the data store in the database while registration & similarly, second & third level will authenticate the entered password by user.
Advantages
- This system uses only security purpose, it uses to all security place.
Provides strong security against bot attacks or hackers. - Hackers are not very easily to hack the security, because their levels are more useful this concept.
- Any hacker if in the extreme case, suppose (although difficult) will cross through the above two mentioned security levels, will definitely not be able to cross the third security level.
- Users can set or upload their own images.
The user will be authenticated as an authentic user, and will be awarded access to the stored information, only after crossing the three security levels. - Protects systems vulnerable to attacks.
- The system is user-friendly and has simple interface.
Limitations
- The only disadvantage is if users forget the password, it cannot retrieve it.